AES is the Advanced Encryption Standard, a standard for cryptography that is used to encrypt data to keep it private. It is a popular cypher, used for many purposes, including the US Government to keep classified data secure.
AES is a symmetric, block cipher which means that blocks of text of a certain size (128 bits) are encrypted, as opposed to a stream cipher where each character is encrypted one at a time. The symmetric part refers to that the identical key is used for the encryption process, as well as to decrypt the message.
- We've also highlighted the best encryption software tools
The quest for better
AES was developed in the late 1990’s to replace the prior encryption standard for the US Government, known as Data Encryption Standard (DES) which was created by IBM in the early 1970’s. It was adopted for US Government use in 1977, but was subsequently demonstrated to be vulnerable to a variety of attacks, including brute force, differential cryptanalysis and linear cryptanalysis, due to the weakness that DES is based on a 56-bit algorithm- considered no longer secure as computer processing power increased.
As an interim measure, in 1998, DES evolved into 3DES, also known as the ‘Triple DES,’ which applied the DES algorithm to the message three consecutive times, with three different encryption keys, to better encrypt the message. The 3DES modification of DES made the message more secure from brute force attacks of contemporary computers.

Fifteen different cryptographic algorithms were proposed to replace DES, in what began a five year process by the US Government. AES was submitted from a pair of Belgian cryptographers, Vincent Rijmen and Joan Daemen, and it became known as the ‘Rijndael proposal,’ from a mash of the two developer’s names.
The AES is an open standard, and the standard itself is not classified. This was done to facilitate public comment to aid in development through transparency, while it was still in the design stage. It was developed by the National Institute of Standards and Technology (NIST), with a goal of ease of use for both the hardware and software. Through this process, some refinements to the original Rijndael were done, including changes to the key and block length to further enhance the security.

The Belgians rise to the top
The NSA was also involved in looking at the fifteen original submissions, and by August of 1999, the field was narrowed to five algorithms, (Rijndael, Serpent, RC6, Twofish and MARS). These then received further analysis, including the strength of the security, ease of implementation, a royalty-free algorithm, and the speed and accuracy for both encryption and decryption. After the analysis ended, the Rijndael cipher emerged as the winner, and it was subsequently rolled out for use in the US Government in 2002, including the NSA and other agencies.
To this day, AES continues to be used for classified documents, and is considered the Federal Information Processing Standard (FIPS). Subsequently it was adopted by the private sector as well, and AES is the most popular cipher for symmetric key cryptography.
How AES works
AES is based on a block cipher, with each having a size of 128 bits. The keys are symmetric, with three different sizes available: 128, 192 or 256 bits, with the latter two used for US government documents designated for their highest level of security, known as ‘Top Secret.’ The original Rijndael cipher had options for both additional block sizes, and key lengths, but these were dropped in favor of standardization on the 128-bit block size, and key lengths of 128, 192 and 256 bits. AES remains the the only publicly available cipher that is approved by the NSA to protect government information at these highest levels of security clearance.
AES uses a substitution permutation network (SPN) block cipher algorithm. The open message gets transformed to a secure message through several steps. It starts with each block of plain text as a standard size. The message is inserted into an array, and then a cipher transformation is done to encrypt the message. Each round of encryption applies substitutions, transpositions and mixing.
Like in the 3DES code that had three rounds of encryption, with AES there are multiple rounds of encryption as well. However, with AES, this is done significantly more than in 3DES, which depends on the key length, with 10 rounds applied for a 128-bit key, 12 rounds for the 192-bit key, and 14 rounds when encrypting via the 256-bit key, accounting for the higher level of security.
During this process, an encryption key gets created, which is required to decrypt the message by the intended recipient; without the encryption key, the message is quite scrambled and unintelligible. Therefore, both the sender, and the recipient must know the same key to be able to encrypt or decrypt the message.
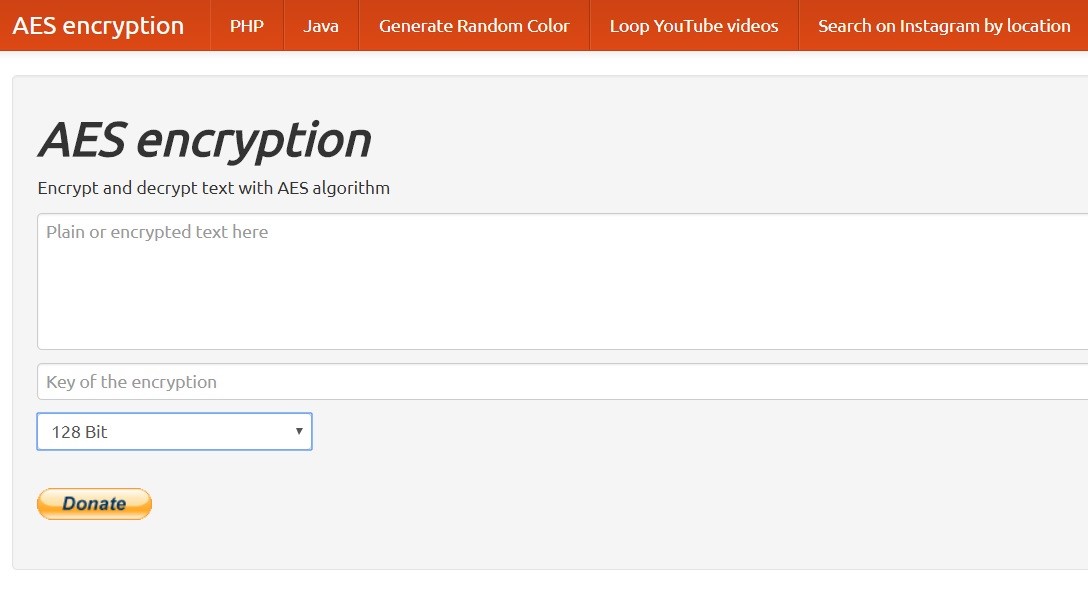
AES for everybody
These days, via the web, AES cryptography can be easily accessed by any user, true to its open source roots. For example, via the website AES Encryption, the message is placed in the text box, a key is entered in the lower box, and the key length is selected; all three lengths are supported: 128, 192 and 256-bit. The button to encrypt or decrypt is selected, and the AES cipher is applied. While this makes AES accessible to public users, the lack of security via a web interface is hardly appropriate for government use.
AES and the internet
While AES was originally developed for US Government applications of classified data, it also gets used to keep file transfers private across the internet. For example, AES gets used when transferring files via an HTTPS connection, the more secure variant of an HTTP connection, which is designed to prevent a man-in-the-middle attack.
Closer to home, AES is also used to encrypt the Wi-Fi on your router, when combined with the popular WPA2 protocol, that gets termed AES/WPA2. The alternate security protocol with WPA2 is TKIP, which is older than AES, and not considered as secure (although is sometimes used for backwards compatibility to older devices). Finally, AES is also used in support of SSL encryption.
Final thoughts
What began as a US Government project to keep their communiqué secure, did that, and so much more as much communication on the modern internet depends on AES, even if many users have not even heard of it. To this day, AES remains the “gold standard” of encryption techniques.
source http://www.techradar.com/news/what-is-aes
No comments:
Post a Comment